Windows
Binary packages of Elasticsearch and Kibana are no part of this distribution. Download them from elastic.co . Supported are the versions 9.1.x, which have been tested explicitly. Compatibility with all 9.1.x versions can be assumed.
| There are several ways to install, configure and run Elasticsearch stack. This documentation provides a simple and direct approach, but the concrete configuration may differ in your environment. |
Installation documentation
Please also get an understanding of installation by reading the according Elasticsearch documentation.
Elasticsearch
After you have unpacked the download package, you can create a Windows service via bin/elasticsearch-service.bat.
By default, Elasticsearch is available at http://localhost:9200/.
|
Elasticsearch normally uses port 9200. Please check if access to this port from outside is allowed by your firewall! In addition, how to configure authenticated access to Elasticsearch is described below. |
Configuration
In addition, you can follow these steps to make your cluster fully functional.
An elasticsearch.yml configuration file can contain this additional information:
xpack.monitoring.collection.enabled: true
xpack.security.authc.api_key.enabled: true
xpack.security.audit.enabled: true
# enabling security is recommended and desired
xpack.security.enabled: true
# this also comprises ssl transport security
xpack.security.transport.ssl.enabled: true
# you may define your own elasticsearch cluster name
cluster.name: <company>-operations
# each node participating in the cluster may receive an individual node name
node.name: analytics-node-01
# define network binding of elasticsearch, defaults to localhost, which is not sufficient if you distribute components across different nodes
# example here: your host is named "elastic-host.example.com"
network.host: "elastic-host.example.com"
# some settings quite specific to the number of nodes participating in your elasticsearch cluster
# if there is only a single node in your cluster, stay with the default "single-node"
# please verify w/ elastic docs: https://www.elastic.co/guide/en/elasticsearch/reference/7.17/bootstrap-checks.html
discovery.type: "single-node"
#discovery.seed_hosts: ["elastic-host.example.com"]
#cluster.initial_master_nodes: ["elastic-host.example.com"]
## Provide external paths for data and log storage
#path.data: E:/service.monitor/data/elastic
#path.logs: E:/service.monitor/logs/elasticEnabling Transport Layer Security (TLS)
Running elasticsearch in production mode requires Transport Layer Security to be enabled. Elastic comes with some scripts to help set up this mode.
# generate new certificate authority
/usr/share/elasticsearch/bin/elasticsearch-certutil ca
# generates X.509 certificates and private keys
/usr/share/elasticsearch/bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12Please also see the Information from Elastic on TLS .
Kibana
Configuration of kibana.yml
Configuration
A kibana.yml configuration file shall contain this additional information/configuration:
server.publicBaseUrl: "http://HOSTNAME:5601"
server.host: "HOSTNAME"
elasticsearch.hosts: ["http://HOSTNAME:9200"]
elasticsearch.username: "kibana_system"
elasticsearch.password: "******"
xpack.encryptedSavedObjects.encryptionKey: ee7b4780fc5cc492e60f365ac12788fa
xpack.reporting.encryptionKey: d4ad47d7ca8b09e650c0f0fa9baad4aa
xpack.security.encryptionKey: 3876cd060838af800da749acc9c604ff
vis_type_vega.enableExternalUrls: trueNSSM via GUI
After unpacking the download package, it makes sense to create a Windows service that can start the process automatically, independent of logged in users. The best way to do this is to use the tool NSSM . The download is unpacked into a folder of the installation.
Calling it from an administrative command line calls the NSSM GUI, which can be used to define further properties of the service execution.
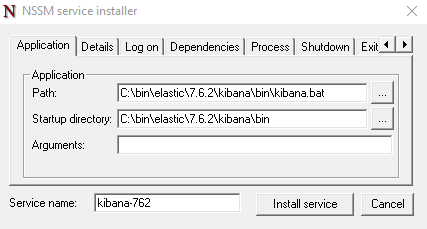
.\bin\nssm.exe install elastic-kibanaThe two screenshots show possible configuration options for the Windows service settings. Setting environment variables is not necessary here.
Set Application Path to the kibana.bat of the concrete version.
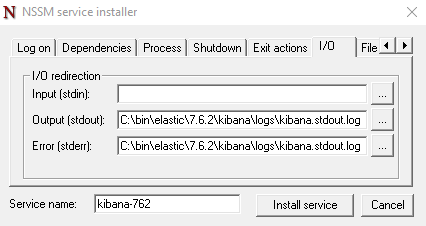
Redirect console output to files.
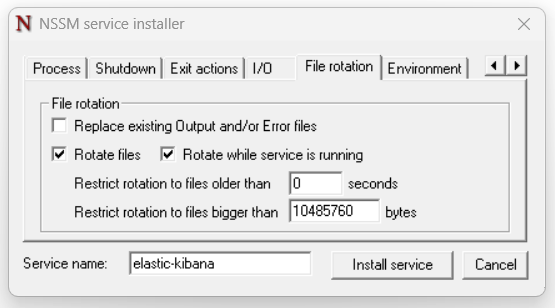
You can define a log file rotation for these files. The value 10485760 bytes corresponds to 10 MB.
NSSM via command line
Experienced users can alternatively call up NSSM via the command line.
nssm.exe install elastic-kibana E:\service.monitor\kibana-9.1.3-windows-x86_64\bin\kibana.bat
nssm.exe set elastic-kibana AppDirectory E:\service.monitor\kibana-9.1.3-windows-x86_64\bin
nssm.exe set elastic-kibana AppExit Default Restart
nssm.exe set elastic-kibana AppStdout E:\service.monitor\logs\kibana\kibana.log
nssm.exe set elastic-kibana AppStderr E:\service.monitor\logs\kibana\kibana-err.log
nssm.exe set elastic-kibana AppRotateFiles 1
nssm.exe set elastic-kibana AppRotateOnline 1
nssm.exe set elastic-kibana AppRotateBytes 10485760
nssm.exe set elastic-kibana DisplayName "Elastic Kibana"
nssm.exe set elastic-kibana ObjectName LocalSystem
nssm.exe set elastic-kibana Start SERVICE_DELAYED_AUTO_START
nssm.exe set elastic-kibana Type SERVICE_WIN32_OWN_PROCESSIn the example above, an elastic-kibana service is created. The installation files are available under E:\service.monitor in version 9.1.3. The details of paths and storage locations must be adapted individually.
The entries of NSSM can be found in the Windows Registry under the key HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.
|