Release Notes 4.15
What’s New
Improved Session Cookie Protection
This version introduces two properties to make it easier protecting the security.manager single sign-on cookie (SSO cookie) from security threats: security.sso.cookie.secure and security.sso.cookie.samesite.
Both properties are available (but deactivated) in the application.properties of new installations.
If you are upgrading security.manager and keeping your application.properties file, add those properties and check if they need to be activated in your environment.
For detailed descriptions of those properties, see Security settings.
Trusted Server Certificates
Server certificate trustworthiness checking for outgoing HTTPS connections is not enabled by default in security.manager.
As of this version, the configuration option security.ssl.trustAny is available in the application.properties.
With this option the verification of server certificates can be activated.
You find a more detailed description of this configuration property in the documentation about Installation.
A new section Security Aspects > Outgoing HTTPS Connections is added to the Installation Guide. This chapter contains detailed information about checking the trustworthiness of server certificates in this product.
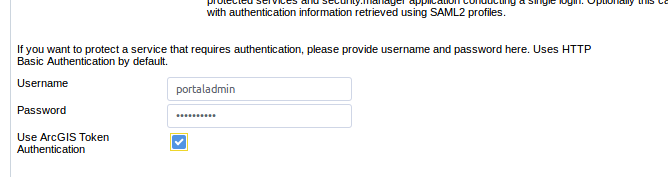
Token Authentication for ArcGIS Server and Portal
It is now possible to let security.manager communicate with ArcGIS Server and Portal by using a technical user. This might be necessary to secure services that are not public on ArcGIS Server.
Credentials of the technical user have to be added when configuring a Protected Service in the Administration Web App.
Cross-Origin Requests to security.manager
security.manager does no longer accept requests from any origin via CORS.
If, for example, a map.apps application hosted on http://mapapps.example.com:8080 tries to use a service secured by security.manager hosted on http://secman.example.com:8080, any requests from map.apps are blocked by the browser.
To allow such requests by the browser, you have to add http://mapapps.example.com:8080 to the new configuration property cors.allowed.origins.
Update Notes
Configuration Changes
- wss.arcgistoken.support.enabled
-
This property has been removed. ArcGIS Token Authentication support is always enabled as of now.
- security.ssl.trustAny
-
New property to toggle certificate validation.
- security.sso.cookie.secure
-
New property to toggle secure flag on SSO cookie issued by security.manager
- security.sso.cookie.samesite
-
New property to toggle sameSite flag on SSO cookie issued by security.manager
- cors.allowed.origins
-
New property to define, from which origins security.manager can be used via CORS
- cors.any.origins
-
New property to define that security.manager can be used via CORS from any origin Do not use it in production environments.
Changelog
4.15.0
New Features and Improvements
|
Introduce CSRF token mechanism in admin JSPs |
|
Authenticate against federated ArcGIS Server |
|
Provide properties to add flags "Secure" and "SameSite=Strict" to domain cookie |
|
Allow CORS configuration in application.properties |
|
Enable token authentication on ArcGIS Server services by default |
|
Don’t use JSESSIONID in URLs to transmit session ID |
Fixed Issues
|
AGS MapServer parent layer links not rendered correctly |
|
Classbreaks elements not rendered correctly on service directory HTML pages |
|
Server error 500 when navigating to enforcement point |
|
Context files written by installer do not contain "useHttpOnly=true" |
|
Layer metadata displays name of and links to forbidden layers |
|
ArcGIS token security allows ArcGIS Server with /arcgis substring only |
|
agstoken and token endpoint is available without token under some circumstances |