Creating Rights for ArcGIS Server
To create policy sets for ArcGIS Server services, select ArcGIS Server from the navigation tree.
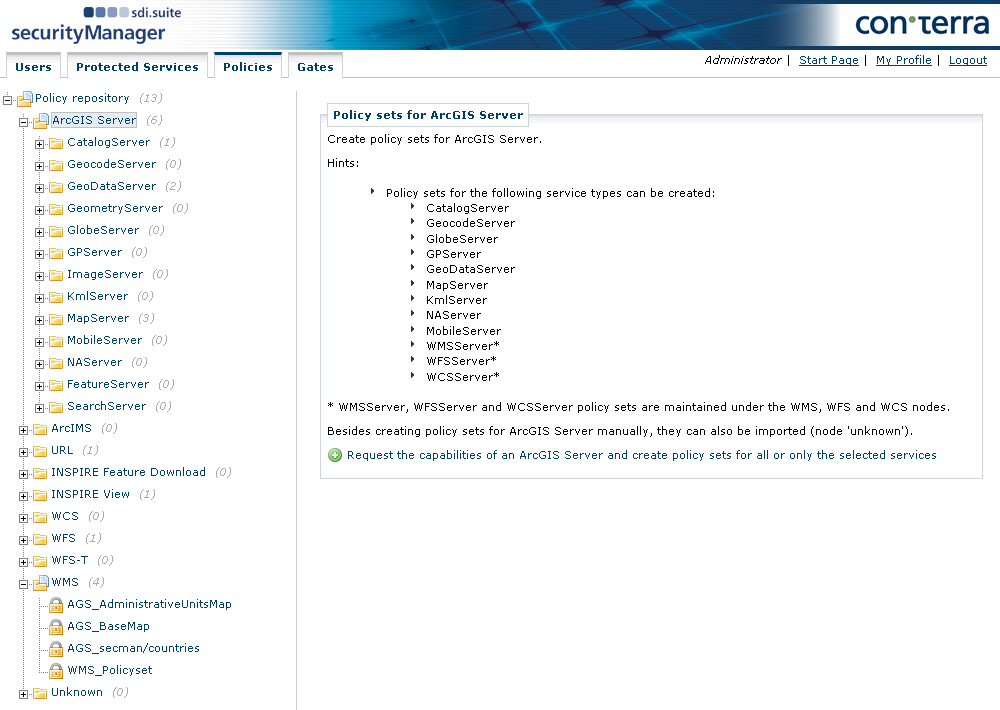
To add a new ArcGIS Server, click +. A dialog is displayed in which you can either select a previously created ArcGIS Server in the Protected Services tab or enter a URL directly in the field URL of the ArcGIS-Server, after first selecting Other in the Protected Service field.
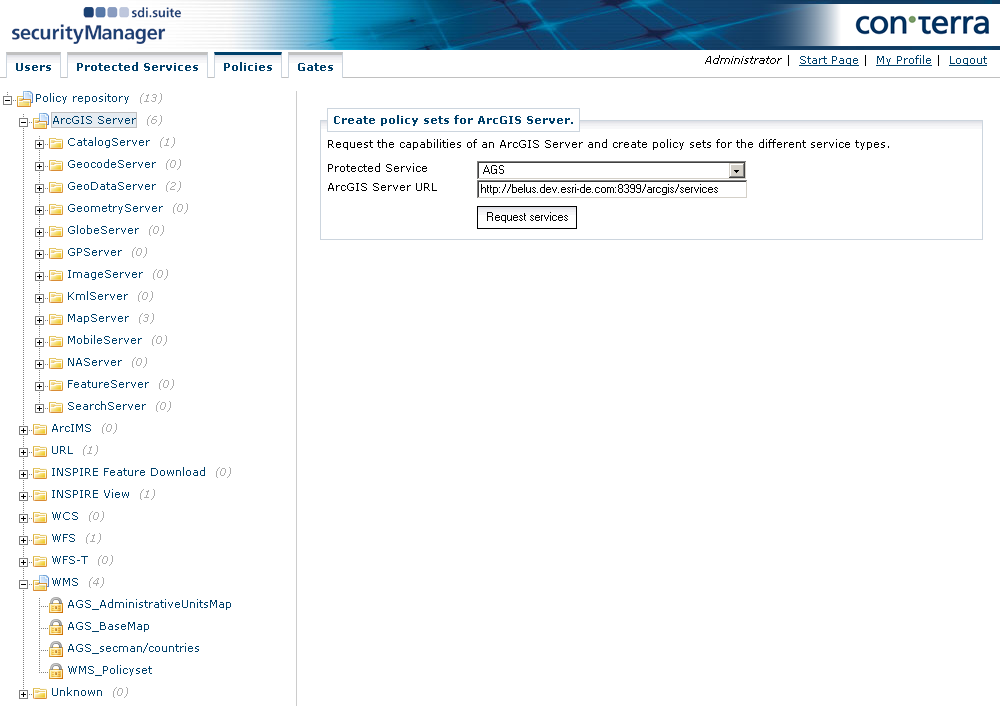
To request and display the available ArcGIS Server services, click Request Services.
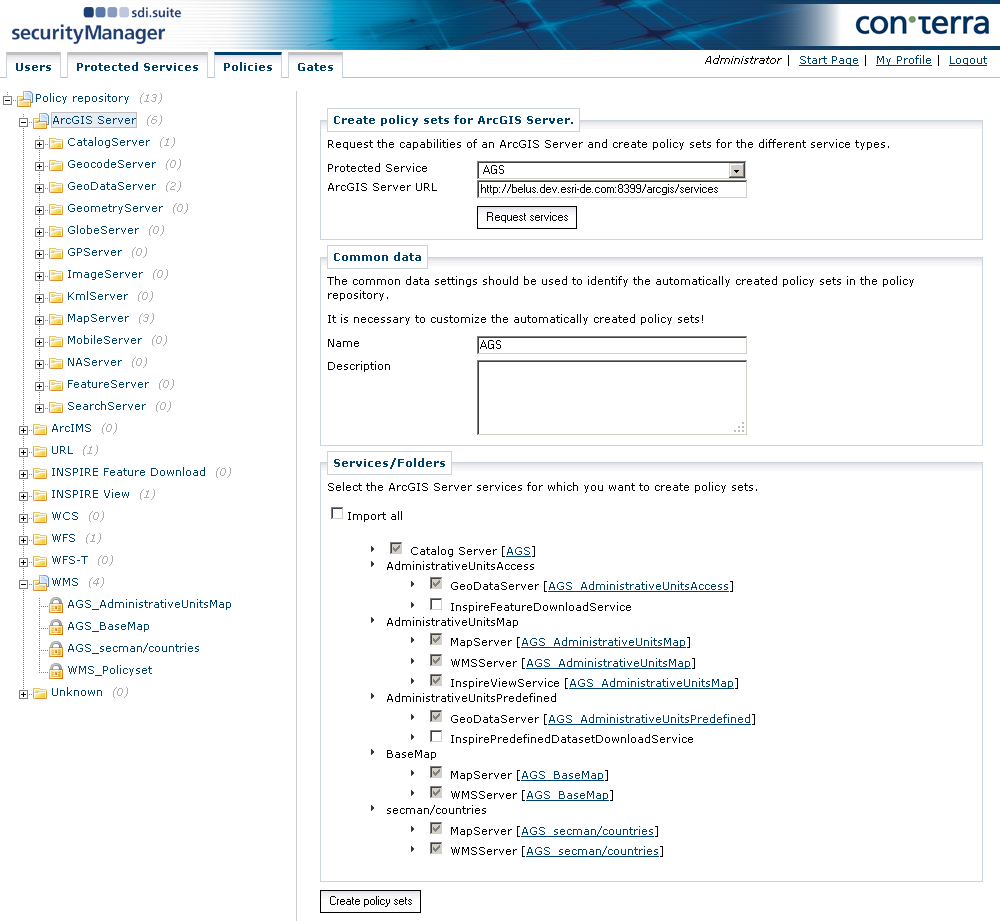
The individual ArcGIS Server services are listed. Select the services that you want to generate policy sets for and click Create policy sets. The policy sets are listed underneath the ArcGIS Server node of the navigation tree.
The generation of policies within these policy sets is done in the same way as for WMS policies.
Group Layer Authorization for MapServer
The following example hierarchy illustrates which layers you need to authorize to restrict access to an entire group of layers:
-
Plants (ID: 0)
-
Crops (ID: 1)
-
Flowers (ID: 2)
-
Hedges (ID: 3)
-
Trees (ID: 4)
-
Conifers (ID: 5)
-
Leaf trees (ID: 6)
-
-
If you want to restrict access to all trees for example, clear all layers of this group (IDs 4, 5 and 6) in the Resources area for the corresponding right.
Definition Queries for MapServer and FeatureServer
ArcGIS Server MapServer/FeatureServer allows the use of filter expressions (definition queries) to filter features from certain layers. The effect is that MapServer/FeatureServer only provides features in accordance with the filter expression. Such filters can be created with ArcMap’s Query Builder.
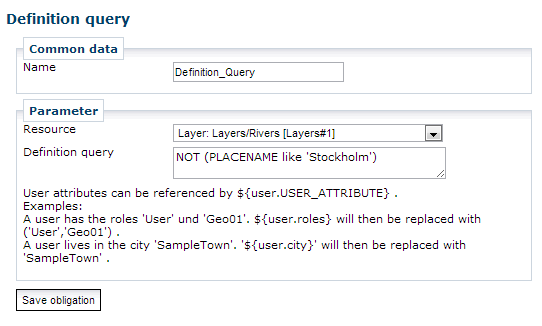
security.manager allows to add these definition queries as an obligation to a policy to restrict access to certain features only. It is recommended to use the Query Builder to create these queries and copy and paste them into the obligation definition.
Furthermore it is possible to reference user attributes in definition queries by using a expression like ${user.USER_ATTRIBUTE}.
A feature has an attribute CITY.
To display features from their home city only to a user, a definition query could look like this:
CITY = '${user.city}'Following user attributes are available (if set):
| Expression | Description |
|---|---|
|
username |
|
given name |
|
family name |
|
phone number |
|
email address |
|
street incl. house number |
|
city |
|
country |
|
gender |
|
roles assigned to the user Because it is possible for a user to be assigned to multiple roles, this expression is expanded to a string like ( |
| Explicitly setting single quotes around expression for string-typed fields in AGS is obliged to the administrator user. The only exception is when using the default expression for the roles attribute. |
Attribute Value Restrictions on Editing Operations
In security.manager you can define which field values are allowed, when editing fields of features provided by a protected feature server.
To use this feature you have to create an obligation of type Attribute Value Restrictions in your FeatureServer policy that defines edit permissions.
Here you have to specify the restrictions that apply to features being edited through a Feature Server request. The restrictions define the range of values accepted for fields of a feature being updated or added.
Restrictions have to be specified as filter expressions in a special format as described in the obligations’s form. Literals are referenced as '?' inside the expression. On service request they are replaced by the literal values given as List of values in the order of their occurrence.
Attribute Restrictions for MapServer and FeatureServer
security.manager allows to limit the visibility of fields inside layers or tables through policy obligations. Being available for MapServer and FeatureServer, the effect of such an obligation is that fields are filtered off service responses and cannot be used in service requests. The result is that a user does not notice that they only get a subset of the available attributes.
Defining Attribute Restrictions in the Policy Administration
To create a new attribute restriction for MapServer or FeatureServer, add a new obligation of the type Attribute Restrictions to an existing policy.
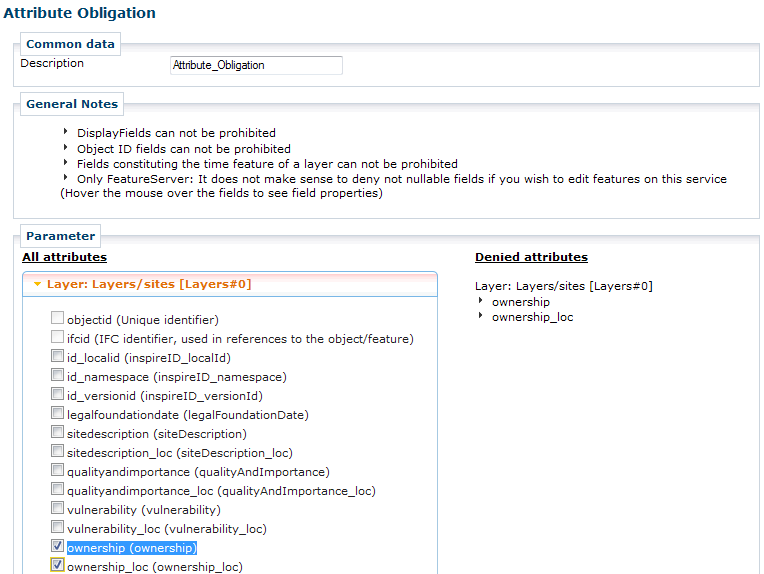
The dialog for defining attribute obligations provides an overview of all layers of the actual ArcGIS Server MapServer or FeatureServer instance. An attribute can be added to the list of denied attributes by activating the belonging checkbox. Clear the attribute’s checkbox to remove the attribute restriction.
Notes
HTML Popups
When an attribute obligation exists for a certain layer on a MapServer, the HTML popup feature for that layer does not return feature information.
Multi-Layer Operations
On MapServer, if denied attribute fields are referenced in operations which operate on multiple layers and it is not possible to assign referenced attributes to requested layers, then the denied attributes are removed from the entire request.
Consider a Find request with parameter layers=0,1 and parameter searchfields=name,class.
If an attribute obligation exists for class on layer 0, but all attributes are allowed on layer 1, class is removed from searchfields although it is allowed for layer 1.
All-Columns-Asterisk-Operator
Requests, which uses the All-Columns-Asterisk-Operator (such as in SELECT * FROM table_name), are rejected as invalid requests and not transferred to the ArcGIS Server.
This action prevents unauthenticated users become aware about restricted attributes or values of them.
Printing Protected Services with the PrintingTools Service
security.manager supports printing a map from a web application with the PrintingTools Service.
The PrintingTools Services is a preconfigured service in the "Utilities" folder of ArcGIS Server.
This service is an ordinary GeoProcessing service (GPServer) that offers a tool for printing maps that is named Export Web Map Task by default.
Because any GeoProcessing service tool can be protected by security.manager, you can also protect the printing task to enforce personalized access to ArcGIS Server-based printing. For any printing task sent to a protected PrintingTools Service that references services made available through the same security.manager instance, the resulting map reflects access permissions as defined for the acting user. To guarantee correct behavior it is necessary to enable "agstoken" authentication in security.manager for the protected ArcGIS Server instances. This is required also if access to the protected PrintingTools Service is made by means of other authentication mechanisms. Otherwise ArcGIS Server is not able to pass information about the requesting user on to security.manager when requesting map data for protected services.
This behavior is true for those geoprocessing tasks having a name starting with "Export Web Map" and the called operation "execute" (REST). On SOAP endpoints the operation name has to be "Execute".