Creating Rights for URLs
For other services or online resources, it is possible to issue policies using generic URL protection. To do this, select URL in the tree view.
Generic URL protection allows the user to define both a base URL and an optional sub-URL. If only the base URL is defined, the policy definition refers exclusively to this URL and no sub-URLs are contained in the policy.
'http://myservice.de'If no sub URLs are defined, the policy does not apply to any URLs derived from them.
-
http://myservice.de/index.html -
http://myservice.de/de/suburl/document.pdf -
http://myservice.de/services/myservice?parameter1=1¶meter2=2
Parameters that are appended to the base URL with a '?' are taken into account, which means that the following example is an integral part of the policy:
-
http://myservice.de?parameter1=1¶meter2=2
If sub-URLs are used, only these are taken into account, which means that the base URL alone is now no longer an integral part of the policy. The wildcards '*' and '/**' might be used ('*' stands for any element in the URL path and '**' stands for any ending in the URL).
Any sub-URLs beginning with http://myservice.de/de are taken into account, for example:
-
http://myservice.de/de/index.html -
http://myservice.de/de/suburl/document.pdf -
http://myservice.de/de?parameter1=1¶meter2=2 -
http://myservice.de/de/service?parameter1=1¶meter2=2
However, the following URL is no longer included:
-
http://myservice.de?parameter1=1¶meter2=2
This example allows any element after the base URL, but in the following level, it is restricted to the ending index.html. This means that the following URLs are an integral part of the license:
-
http://myservice.de/de/index.html -
http://myservice.de/en/index.html -
http://myservice.de/fr/index.html
On the other hand, the following URL is not taken into account:
-
http://myservice.de/de/document.pdf
This example demonstrates that that it is also possible to use concatenated wildcards. The following URLs comply with this definition:
-
http://myservice.de/de/suburl/index.html -
http://myservice.de/en/suburl/index.html -
http://myservice.de/de/suburl/document.pdf -
http://myservice.de/fr/suburl/suburl2/index.html -
http://myservice.de/sonst/suburl/suburl2?parameter1=1¶meter2=2
However, the following URLs are not taken into account:
-
http://myservice.de/suburl/index.html -
http://myservice.de/index.html -
http://myservice.de?parameter1=1¶meter2=2
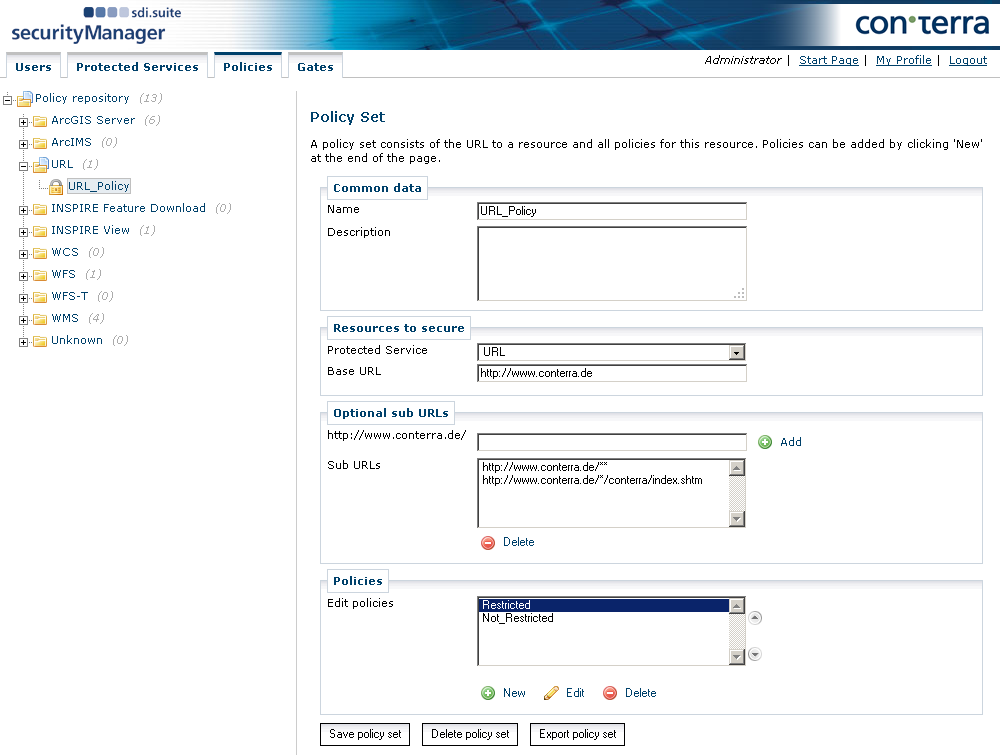
The URLs entered are listed as resources and can each be given either blanket authorization or authorized for certain actions only.
The actions available are HTTP GET, HTTP POST, HTTP PUT and HTTP DELETE.
The latter two actions are not supported by WSS.
security.manager supports further access protection mechanisms for all Java-based web applications, in addition to the WSS.
Policies containing HTTP PUT or HTTP DELETE are rejected by the WSS if such a request is made.
In a response document for a protected service, links are replaced for the purpose of hiding them from external view. Instead, the URL of the web security client or enforcement is used, depending on the method of access selected. All absolute URLs beginning with the URL of the protected service are replaced as are all relative URLs beginning with a '/'. Links to another web context or an external resource are ignored and transported with no changes.
The URL is only replaced when the response document of the protected service supports one of the following media types: text/html, text/xml, text/plain, application/xml, application/xhtml+xml, application/x-httpd-php, text/javascript, text/vnd.wap.wml or application/x-www-form-urlencoded.